The following is a walk through on how to solve the Leviathan wargame featured on Overthewire.org. For this wargame, we ssh on port 2223 to access the levels. Passwords for each level reside in the /etc/leviathan_pass directory. Files for each level reside in the /home directory.
The username and password is provided for level 0.
username: leviathan0
password: leviathan0
Level 0
ssh levianthan0@leviathan.labs.overthewire.org -p 2223
When prompted, enter the password ‘leviathan0’
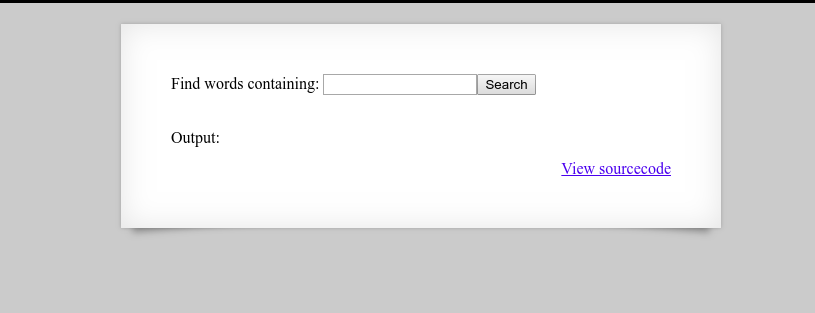
Running la -la we’ll check what’s in our directory:
leviathan0@leviathan:~$ ls -la
total 24
drwxr-xr-x 3 root root 4096 Nov 13 16:03 .
drwxr-xr-x 10 root root 4096 Nov 13 16:03 ..
drwxr-x— 2 leviathan1 leviathan0 4096 Nov 13 16:03 .backup
-rw-r–r– 1 root root 220 Sep 1 2015 .bash_logout
-rw-r–r– 1 root root 3771 Sep 1 2015 .bashrc
-rw-r–r– 1 root root 655 Jun 24 2016 .profile
The .backup directory looks promising.
leviathan0@leviathan:~$ cd .backup/
leviathan0@leviathan:~/.backup$ ls
bookmarks.html
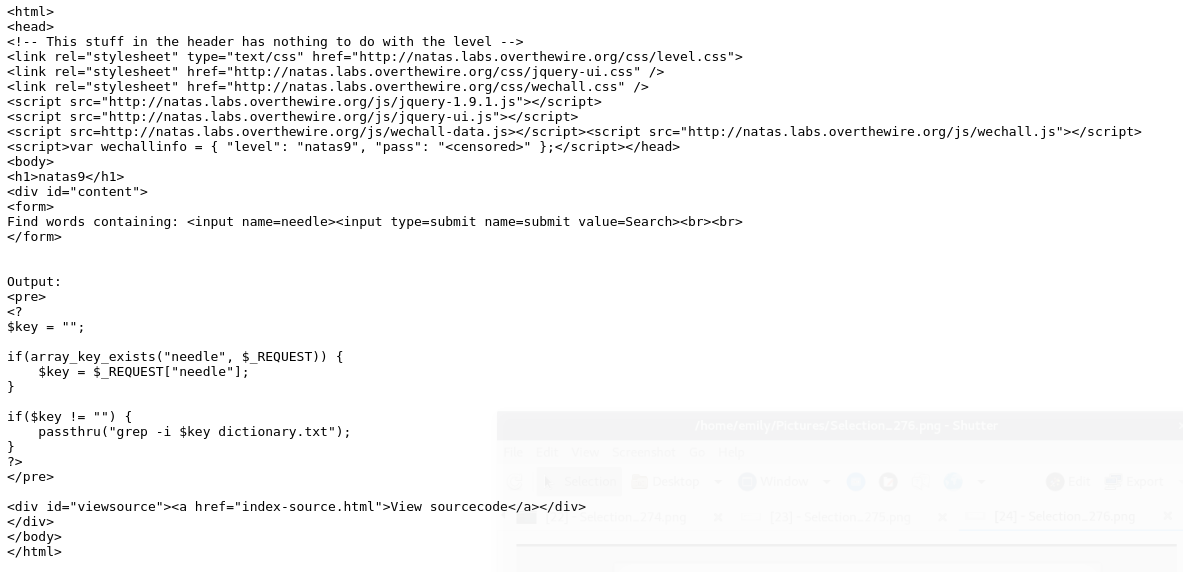
cat bookmarks.html and run a search in your console for the word ‘password’. You will find the following line:
the password for leviathan1 is rioGegei8m
Level 2
ssh leviathan2@leviathan.labs.overthewire.org -p 2223
When prompted enter the password we found in the previous level:
rioGegei8m
Running ls we see an executable in our folder named ‘check’. Running ltrace on the executable gives us the following information:
leviathan1@leviathan:~$ ltrace ./check
__libc_start_main(0x804858d, 1, 0xffffd6f4, 0x8048670
printf(“password: “) = 10
getchar(0x80486f0, 0, 0xf7e45830, 0x80486bbpassword: nnnn
) = 110
getchar(0x80486f0, 0, 0xf7e45830, 0x80486bb) = 110
getchar(0x80486f0, 0, 0xf7e45830, 0x80486bb) = 110
strcmp(“nnn”, “sex”) = -1
puts(“Wrong password, Good Bye …”Wrong password, Good Bye …
) = 29
+++ exited (status 0) +++
First, we must understand what the ‘strcmp’ function does.
strcmp(“str1”, “str2”)
This function starts comparing the first character of each string. If they are equal to each other, it continues with the following pairs until the characters differ or until a terminating null-character is reached.
From this we can see the executable prompts us for the password and compares it against the word “sex”. Therefore, entering “sex” as the password will give us a shell. From there all we have to do is cat the contents of ‘leviathan2’ from the /etc/leviathan_pass directory.
leviathan1@leviathan:~$ ./check
password: sex
$ cat /etc/leviathan_pass/leviathan2
ougahZi8Ta
Level 3
ssh leviathane@leviathan.labs.overthewire.org -p 2223
When prompted, enter the password we identified in the previous level:
ougahZi8Ta
Let’s run ‘ls -la’ to see what’s inside our directory and view the permissions of the files.
leviathan3@leviathan:~$ ls -la
total 32
drwxr-xr-x 2 root root 4096 Nov 13 16:03 .
drwxr-xr-x 10 root root 4096 Nov 13 16:03 ..
-rw-r–r– 1 root root 220 Sep 1 2015 .bash_logout
-rw-r–r– 1 root root 3771 Sep 1 2015 .bashrc
-rw-r–r– 1 root root 655 Jun 24 2016 .profile
-r-sr-x— 1 leviathan4 leviathan3 10176 Nov 13 16:03 level3
We find another executable entitled ‘level3’. Let’s run it to see what it does.
leviathan3@leviathan:~$ ./level3
Enter the password> 123
bzzzzzzzzap. WRONG
Now run an ltrace to see which libraries are being called.
leviathan3@leviathan:~$ ltrace ./level3
__libc_start_main(0x804867e, 1, 0xffffd6f4, 0x8048750
strcmp(“h0no33”, “kakaka”) = -1
printf(“Enter the password> “) = 20
fgets(Enter the password> 123
“123\n”, 256, 0xf7fc75a0) = 0xffffd4ec
strcmp(“123\n”, “snlprintf\n”) = -1
puts(“bzzzzzzzzap. WRONG”bzzzzzzzzap. WRONG
) = 19
+++ exited (status 0) +++
Examining the code, we can see that after we enter the password ‘123’, strcmp compares it against the string ‘snlprintf’. Likewise, if we enter ‘snlprintf’ as the password, it should work.
leviathan3@leviathan:/tmp/emily1$ ./level3
Enter the password> snlprintf
[You’ve got shell]!
From there, we simply cat the contents of the file /etc/leviathan_pass/leviathan4
$ cat leviathan4
vuH0coox6m
Level 4
ssh leviathan4@leviathan.labs.overthewire.org -p 2223
When prompted, enter the password we located in the previous level:
vuH0coox6m
Run ls -la to see what is inside our directory.
leviathan4@leviathan:~$ ls -la
total 24
drwxr-xr-x 3 root root 4096 Nov 13 16:03 .
drwxr-xr-x 10 root root 4096 Nov 13 16:03 ..
-rw-r–r– 1 root root 220 Sep 1 2015 .bash_logout
-rw-r–r– 1 root root 3771 Sep 1 2015 .bashrc
-rw-r–r– 1 root root 655 Jun 24 2016 .profile
dr-xr-x— 2 root leviathan4 4096 Nov 13 16:03 .trash
The trash directory looks interesting, let’s change into it.
cd .trash
Run ls -la again.
leviathan4@leviathan:~/.trash$ ls -la
total 16
dr-xr-x— 2 root leviathan4 4096 Nov 13 16:03 .
drwxr-xr-x 3 root root 4096 Nov 13 16:03 ..
-r-sr-x— 1 leviathan5 leviathan4 7460 Nov 13 16:03 bin
We see an executable called bin, running it outputs the following:
leviathan4@leviathan:~/.trash$ ./bin
01010100 01101001 01110100 01101000 00110100 01100011 01101111 01101011 01100101 01101001 00001010
Awesome! Let’s convert that binary to text using an online application. Doing so outputs the password to level 5:
Tith4cokei
Level 5
In our directory we find another executable ‘leviathan5’. Let’s run it:
leviathan5@leviathan:~$ ./leviathan5
Cannot find /tmp/file.log
Now use ltrace to see what libraries are being used:
leviathan5@leviathan:~$ ltrace ./leviathan5
__libc_start_main(0x80485dd, 1, 0xffffd6e4, 0x8048680
fopen(“/tmp/file.log”, “r”) = 0
puts(“Cannot find /tmp/file.log”Cannot find /tmp/file.log
) = 26
exit(-1
+++ exited (status 255) +++
leviathan5@leviathan:~$
As we can see, the executable opens and reads the contents of /tmp/file.log.
I wonder if we can copy /etc/laviathan_pass/leviathan6 to the /tmp directory and then rename it file.log. Let’s try:
leviathan5@leviathan:~$ cp /etc/leviathan_pass/leviathan6 /tmp
cp: ‘/etc/leviathan_pass/leviathan6’ and ‘/tmp/leviathan6’ are the same file
leviathan5@leviathan:~$ mv /tmp/leviathan6 /tmp/file.log
Now let’s run the executable again:
leviathan5@leviathan:~$ ./leviathan5
UgaoFee4li
Hooray!
Level 6
ssh leviathan6@leviathan.labs.overthewire.org -p 2223
When prompted enter the password we identified in the previous level:
leviathan5@leviathan:~$ ./leviathan5
UgaoFee4li
In our directory, we find another executable called leviathan6. Running it provides the following output:
leviathan6@leviathan:~$ ./leviathan6
usage: ./leviathan6
Run ltrace to see which libraries are being used:
leviathan6@leviathan:~$ ltrace ./leviathan6
__libc_start_main(0x804853d, 1, 0xffffd6e4, 0x80485d0
printf(“usage: %s \n”, “./leviathan6″usage: ./leviathan6
) = 35
exit(-1
+++ exited (status 255) +++
No helpful information can be infered. Let’s try and bruteforce the 4 number code using a simple bash script.
First make a temporary directory under /tmp and use nano to create a file named ‘brute.sh’.
leviathan6@leviathan:~$ mkdir /tmp/emily2
leviathan6@leviathan:~$ cd /tmp/emily2
leviathan6@leviathan:/tmp/emily2$ nano /tmp/emily2/brute.sh
Unable to create directory /home/leviathan6/.nano: Permission denied
It is required for saving/loading search history or cursor positions.
Press Enter to continue
In the editor we create our simple script:
#! /bin/bash
for a in {0000..9999}
do
~/levianthan6 $a
done
Save the script and run chmod +x to make it executable.
Run the script, after a few seconds we can see the 4 digit code has been bruteforced and we have a shell, now all we have to do is run:
cat /etc/leviathan_pass/leviathan7
ahy7MaeBo9
Level 7
ssh levianthan7@leviathan.labs.overthewire.org -p 2223
When prompted enter the password we located in the previous level:
ahy7MaeBo9
Then run ls to see what’s in our directory. I see a file named ‘CONGRATULATIONS’, I cat it to see what it says:
leviathan7@leviathan:~$ ls
CONGRATULATIONS
leviathan7@leviathan:~$ cat CONGRATULATIONS
Well Done, you seem to have used a *nix system before, now try something more serious.
Hooray! We have defeated the Laviathan Wargame on Overthewire.org! Super easy, huh?

































You must be logged in to post a comment.