The following is my write up to solving the challenges 0-10 in Natas Wargame presented by overthewire.org
Level 1
Logining with natas0, natas0 like directions say. A pop up box tells me the password is somewhere on that page. Inspecting the source, I can see the password.

gtVrDuiDfck831PqWsLEZy5gyDz1clto
Level 2
Viewing the source code I find a link to another file. Navigating to the /file directory I get the password to level 3.

sJIJNW6ucpu6HPZ1ZAchaDtwd7oGrD14
Level 3
Upon logging into level 3 and viewing the source code I find a clue: “…not even Google will find it this time.”

A robots.txt file lists the files on the website that are not to be crawled by Google. Browsing to robots.txt, I see that a directory called ‘s3cr3t’ is referenced. Upon navigating to that directory, I see a ‘password’ file. Clicking it gives me the password to the next level.
Z9tkRkWmpt9Qr7XrR5jWRkgOU901swEZ
Level 4
After logging in I’m presented with the following:

For this I installed the Firefox addon ‘Tamper Data’ which allows me to capture and edit my http request before it is sent to the server. I change the ‘referrer header’ field to http://natas5.natas.labs.overthewire.org and refresh the page.
Access granted. The password for natas5 is iX6IOfmpN7AYOQGPwtn3fXpbaJVJcHfq
Level 5
After logging in to level 5, I’m presented with the following:

Looking at the source code doesn’t provide any further clues. For this challenge I installed a chrome extension that allowed me to edit the cookie and change the ‘logged in’ variable from 0 to 1. After reloading the page, voila, I’m presented with the password to the next level.
Level 6




Level 7


Level 8
Logging into level 8, I’m presented with the following:
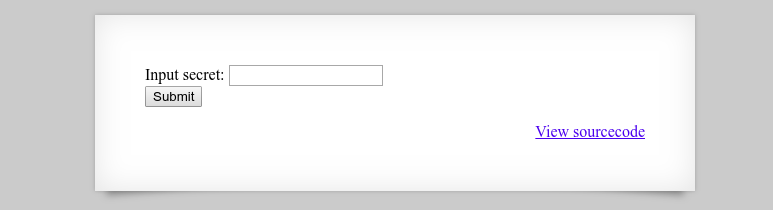
Checking out the sourcecode I’m given a clue:
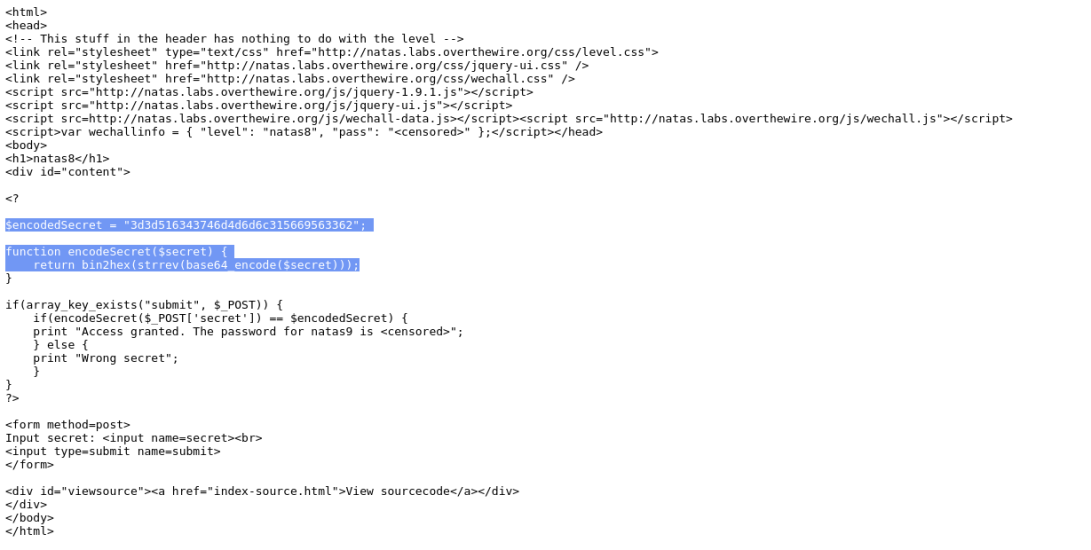
I’m given the secret in encoded form, the methods used to encode it, and the order in which the methods were applied. To solve this level, I run php in interactive mode (-a) to decode the secret using the following commands:
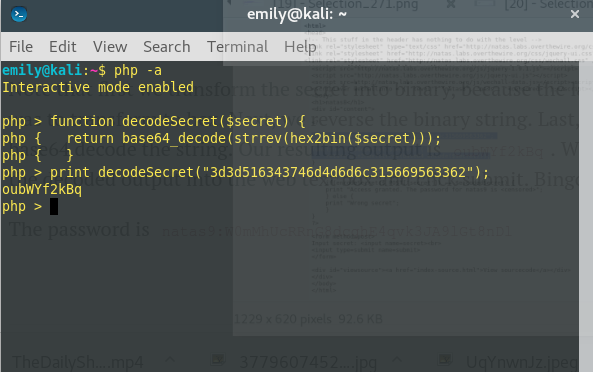
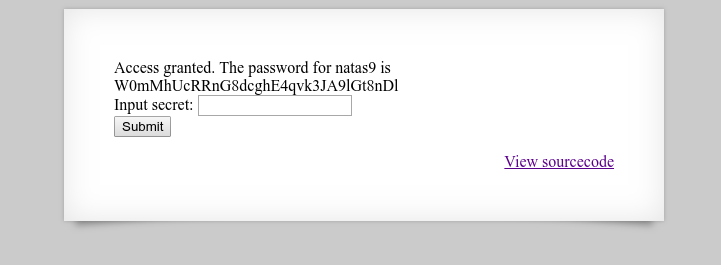
I submit the secret ‘oubWYf2kBq’ and receive the password for the next level.
Level 9
Upon logging in to level 9, I am presented with the following:
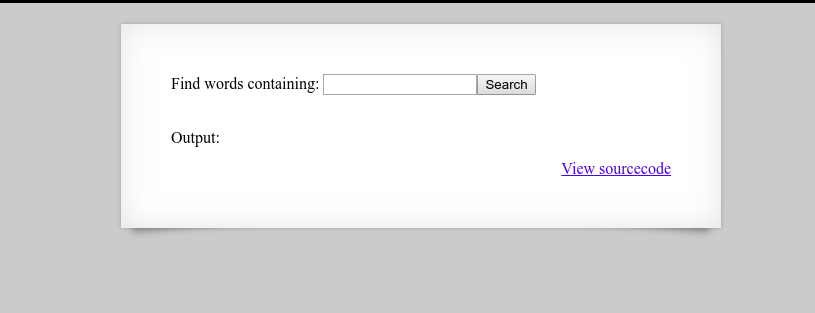
Checking out the source code I see another php script is being used:
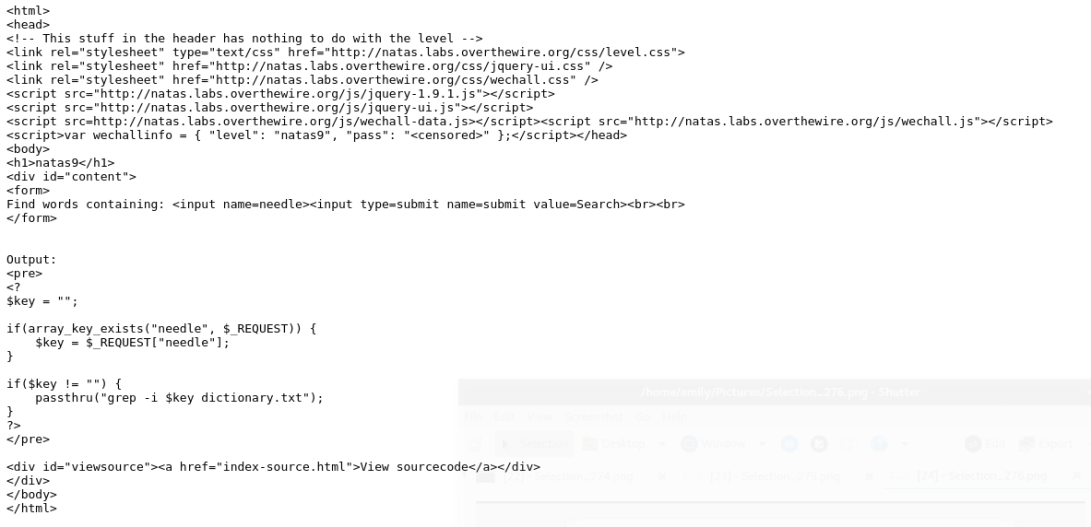
I see that the script is greping the dictionary file. I can chain commands together by using the shell command separator ;. Thinking back to Natas 7, I learned that the passwords are stored in /etc/natas_webpass/respectiveLevel and construct a chained command using this knowledge:
grep-i ; cat/etc/natas_webpass/natas10# dictionary.txt
I used an additional argument in our command chain (#) to comment anything after that operator. Thus, restricting my search to only /etc/natas_webpass/natas10. From there I am given my password to the next level:
nOpp1igQAkUzaI1GUUjzn1bFVj7xCNzu
Level 10
You must be logged in to post a comment.