Level 1
Challenge:
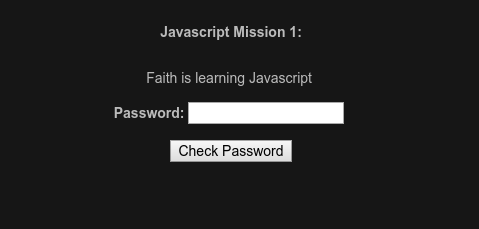
This level is super easy. All you have to do is check the source code for the answer. You will see the following:
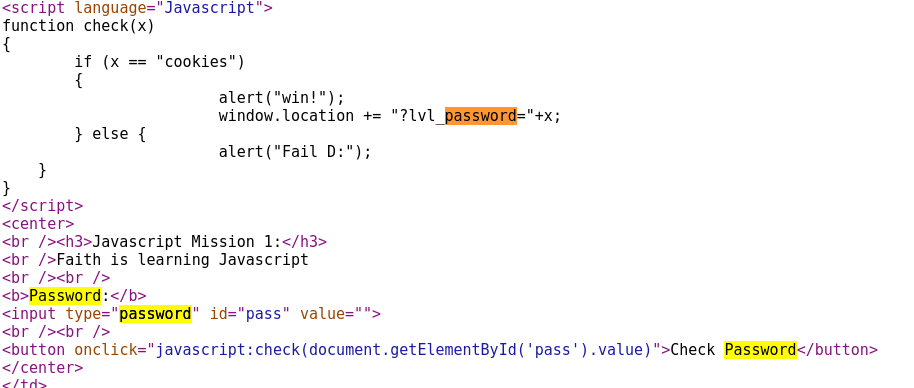
As we can see, the function check(x) determines if x == cookies, if so we will get an alert that says ‘win!’. Let’s enter ‘cookies’ as our password. Bingo!
Level 2
Challenge:
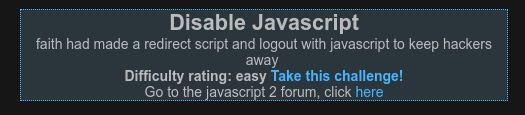
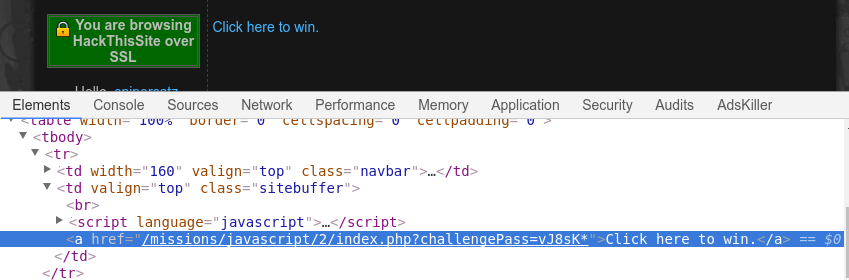
We need to disable javascript to complete the mission. You can download a browser extension that allows you to do so. I used the google chrome extension ‘quick javascript switcher’ to switch off javascript. Next I click ‘take this challenge’ and am presented with the following link that says ‘click here to win!’ Right click your mouse and select inspect. Expand the code and you will find the following link. Clicking it will successfully complete the challenge.
Level 3
Challenge:
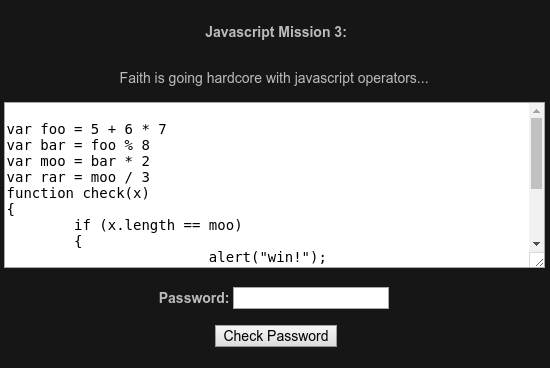
All this level takes to solve it is some simple math. We see the correct answer is the length of value ‘moo’. Let’s solve for ‘moo’.
foo = 47
bar = 47%8 = 7
moo = 7 * 2 = 14
Entering a password with a length of 14 will successfully complete the challenge.
Level 4
Challenge:
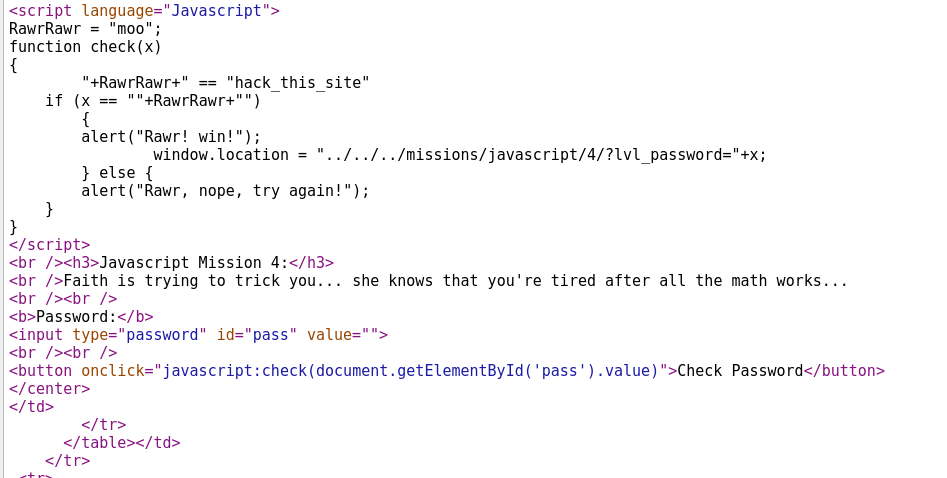
Viewing the sourcecode we can see once again, function check(x) checks to see whether the password = RawrRawr. In the very first line of the code we see RawrRawr = moo. Entering moo should allow us to successfully beat the mission.
Level 5
Challenge:
Let’s check out the source code:
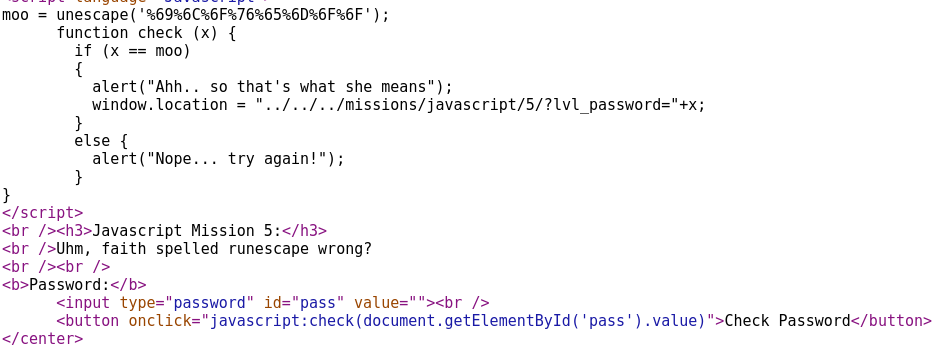
We can see the function check(x) checks to see whether x == moo and if so we’re able to successfully beat the challenge. Line one tells us the unescaped value of moo which appears to be url encoded. Using an online url decoder app, we can determine the password is ‘ilovemoo’.
Level 6
Challenge:
Let’s view the source code:
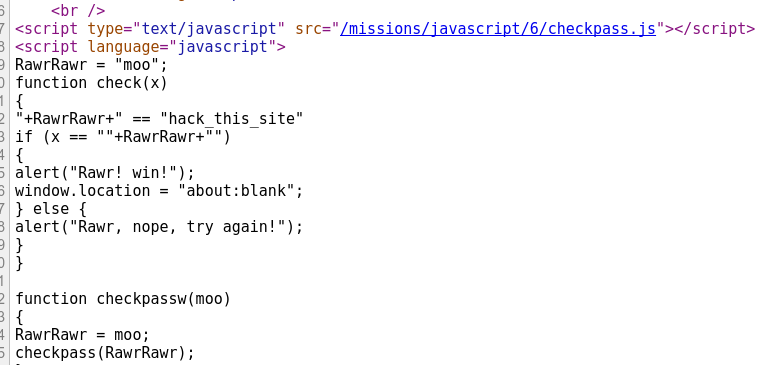
This code is all messed up, but thinking it through we can see we need to navigate to
https://hackthissite.org/missions/javascript/6/checkpass
to get the solution for the level.
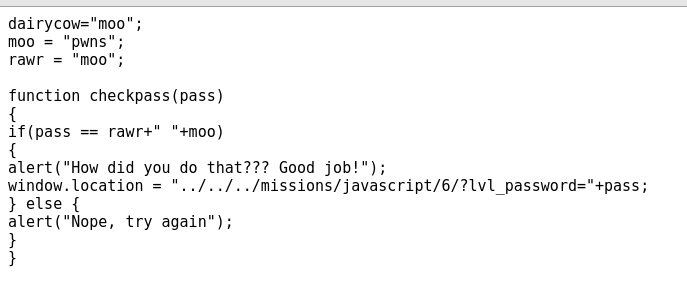
The function checkpass(pass) says if pass == rawr+” “+moo, we’ve successfully defeated the challenge. Above the code we can see rawr = “moo” and moo = “pwns”. So if we enter moo pwns as the password it should be correct…and it is!
Level 7
Challenge:
Viewing the source code shows the following:
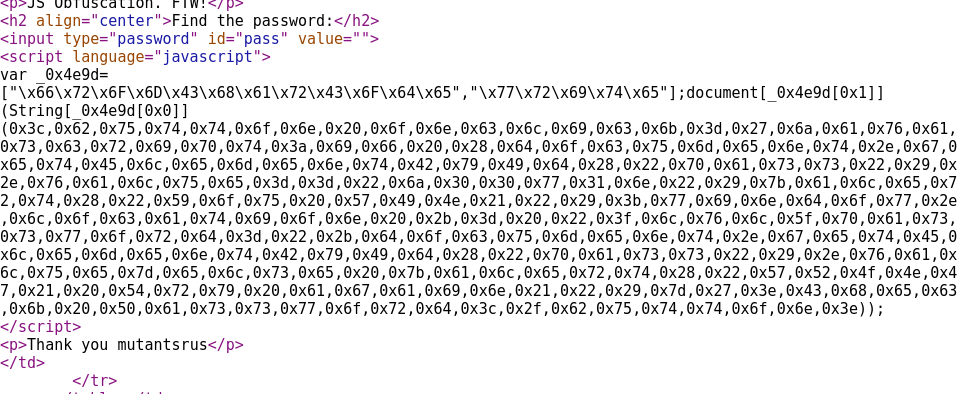
Clearly the javascript for this level’s password has been obfuscated. We can use an online app to deobfucate it. The result is:
< button onclick = ‘javascript:if (document.getElementById(“pass”).value==”j00w1n”){alert(“You WIN!”);window.location += “?lvl_password=”+document.getElementById(“pass”).value}else {alert(“WRONG! Try again!”)}’ > Check Password < /button>
We can see the script checks to see if the value we enter equals j00w1n. If so, we get the alert “You win!” in your browser. Let’s try that password to successfully complete the challenge.